AWS Lambda’s pay-per-use model promises cost efficiency, but hidden traps—cold starts, over-provisioned memory, and recursive triggers which can explode budgets overnight. Global teams from Tokyo to Berlin report 40-70% cost reductions after implementing these AWS Lambda cost optimization strategies, without sacrificing performance.
The Serverless Cost Paradox
Lambda’s pricing seems simple:
- $0.20 per 1M requests
- $0.0000166667 per GB-second
Yet real-world bills tell a different story. When Adobe’s S3-triggered Lambdas recursively invoked themselves in 2019, they generated a $500,000 overnight bill. More commonly:
- 68% of Lambda workloads overspend on memory (Datadog Analysis)
- VPC-related costs exceed compute costs in 3 out of 5 deployments
- Unoptimized logging adds 20-30% to bills via CloudWatch
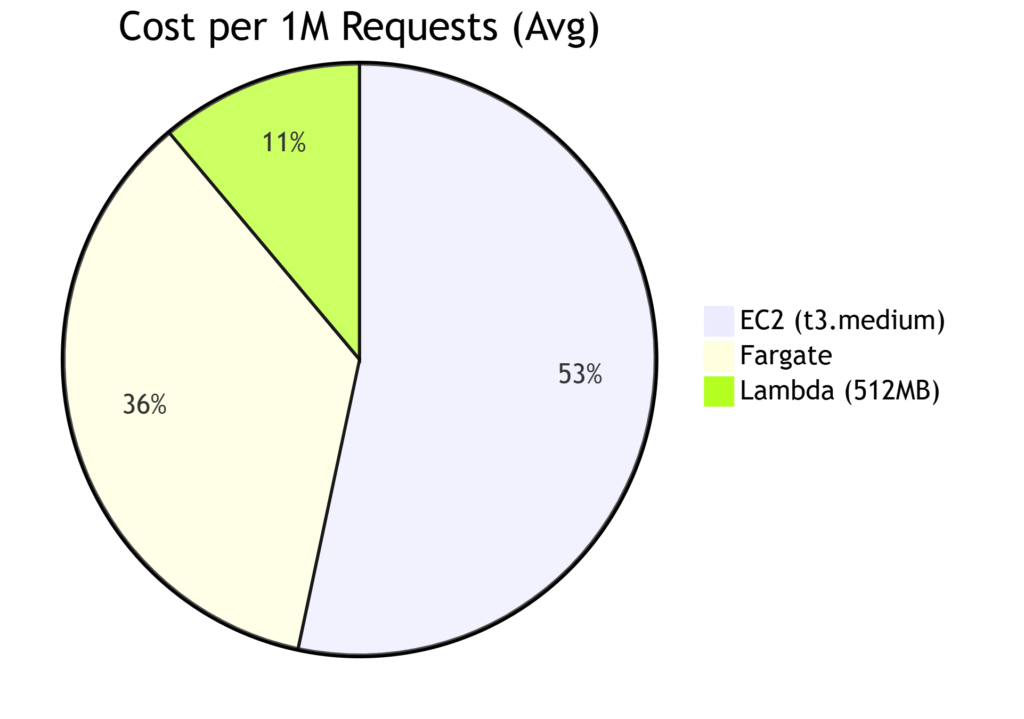
Global Cost-Benefit Analysis
| Metric | Lambda | EC2 (t3.medium) | Containers |
| Cost/1M Reqs | $1.20 | $16.80 | $9.40 |
| Cold Starts | 100ms – 5,000ms | 0ms | 200ms – 1,000ms |
| Ops Overhead | Low (No servers) | High (OS Patches) | Medium (Orchestration) |
5 AWS Lambda Cost Optimization Hacks (With Real-World Examples)
1. Right-Sizing: The Memory/Performance Tradeoff
Why It Matters:
Lambda charges per GB-second, but higher memory doesn’t always mean better performance. Oversizing is the #1 cost killer.
How To Optimize:
- Benchmarking Tool: Use AWS Lambda Power Tuner (Open-source)
Run with 100 executions per memory setting:
aws lambda update-function-configuration –function-name MyFunction –memory-size 1024 - Sweet Spot: Most workloads peak at 1024-1536MB. Example:
- Before: 3008MB → $28.80 per 1M requests
- After: 1024MB → $9.80 per 1M requests (66% savings)
- Pro Tip: For CPU-bound tasks (e.g., image processing), test 1792MB – AWS allocates vCPUs proportionally.
2. Cold Start Elimination: Beyond Provisioned Concurrency
The Problem:
Cold starts add 500ms-10s latency and increase costs when functions scale up.
Solutions:
| Method | Cost Impact | Best For |
|---|---|---|
| Provisioned Concurrency | $0.015/GB-hour | Production APIs |
| SnapStart (Java-only) | Free | Java workloads |
| Ping Keep-Alive | $0.0000002/request | Non-critical jobs |
Implementation:
YAML
# serverless.yml example
provider:
provisionedConcurrency: 5 # Always keep 5 instances warmGlobal Case: A Tokyo-based fintech reduced cold starts from 3.2s to 200ms using SnapStart, saving $4K/month.
3. Logging Optimization: Escape CloudWatch Pricing
The Shock: CloudWatch Logs costs 20x more than S3 ($0.50 vs $0.023/GB).
Step-by-Step Fix:
- Create Kinesis Firehose Delivery Stream
python
firehose.put_record( DeliveryStreamName=’lambda-logs’, Record={‘Data’: json.dumps(log_event)} - Set Retention Policy:
bash
aws logs put-retention-policy –log-group-name “/aws/lambda/MyFunction” –retention-in-days 3 - Alternative: Use AWS Lambda Extensions for real-time log filtering.
Savings Example: 100GB logs/month → $50 (CloudWatch) vs $2.30 (Firehose+S3).
4. VPC Avoidance: NAT Gateway Trap
Why It Hurts:
Every Lambda in a VPC needs a NAT Gateway ($0.045/hour + $0.045/GB data).
Workarounds:
- Option 1: Use VPC endpoints ($0.01/GB) for AWS services
- Option 2: Move non-VPC needs to API Gateway (Free internal calls)
- Option 3: Deploy in us-east-1 (Lower NAT Gateway costs)
Data: Removing VPC reduced a German auto manufacturer’s bill by $18K/month.
5. Error Handling: Stop Retry Storms
The Danger:
A failing Lambda triggering itself can create infinite loops.
Prevention Framework:
- Dead Letter Queues (DLQ):
yaml
# serverless.yml
functions: processor: onError: arn:aws:sqs:us-east-1:123456789:dlq - Exponential Backoff:
python
import random
def handler(event, context): try: # Your code except Exception: wait = min(2 ** event[‘attempts’], 300) time.sleep(wait + random.uniform(0, 1)) - Circuit Breaker Pattern:
python
if event.get(‘failures’, 0) > 5: send_to_dlq(event) return
Global Pitfalls & Fixes
Pitfall #1: Recursive Triggers (The $500K Nightmare)
What Happens:
Lambda writes to S3 → Triggers new Lambda → Writes again → Infinite loop.
Real Incident:
Adobe’s 2019 bill: 1 misconfigured S3 event → 72 hours of recursion → $500K.
Prevention Checklist:
✅ Prefix/Suffix Filters:
yaml
s3:
events:
- s3:ObjectCreated:*
rules:
- prefix: input/ # Only trigger for 'input/' folder
- suffix: .json # Only process JSON files
✅ CloudTrail Alerts: Monitor for abnormal invocation spikes.
✅ S3 EventBridge Rules: Add conditional logic before invoking Lambda.
Pitfall #2: Over-Privileged IAM Roles (Crypto-Mining Attack Vector)
The Risk:
A compromised Lambda with s3:* permissions can encrypt all buckets for ransom.
Documented Attack:
2023 Sysdig report found 41% of Lambdas had admin-equivalent roles.
Least-Privilege Template:
json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": "arn:aws:s3:::my-bucket/uploads/*"
}
]
}
Tools:
- AWS IAM Access Analyzer (Scans unused permissions)
iam-lint(Open-source policy validator)
Pitfall #3: Ignoring Timeout Bloat (The Silent Killer)
The Issue:
Default 3-second timeouts force Lambdas to wait idle, billing you for unused time.
Case Study:
An Australian SaaS startup saved $7K/month by reducing timeouts from 3s → 300ms for 80% of functions.
Optimization Guide:
- Set Realistic Timeouts:
bash
aws lambda update-function-configuration –function-name MyFunction –timeout 10 - Monitor with CloudWatch Metrics:
Durationshould be << configured timeout- Watch for
Throttlesindicating too-short timeouts
- Architecture Fix: For long tasks:
- Step Functions (Up to 1-year runtime)
- SQS → EC2 for >15min jobs
AWS Lambda Cost Optimization for High-Traffic Applications
The 3-Tier Optimization Framework
- Infrastructure Layer:
- ARM Graviton Processors: 20% cheaper than x86 (benchmark with
aws lambda update-function-configuration --architectures arm64) - Multi-Region Deployment: Route traffic to cheaper regions (ap-south-1 is 14% cheaper than us-east-1)
- ARM Graviton Processors: 20% cheaper than x86 (benchmark with
- Code Layer:
Optimized Python example:
import boto3 from functools
import lru_cache @lru_cache(maxsize=1) # Reuse connections
def get_s3_client(): return boto3.client(‘s3′, region_name=’ap-south-1’)
def handler(event, context): s3 = get_s3_client() # Cached call - Orchestration Layer:
- SQS Batching: Process 10,000 records in one invocation vs 10,000 invocations
- Step Functions Express: 50% cheaper than standard for <5min workflows
Monitoring & Continuous Optimization
The 4 Key Metrics to Track Daily

- Cost Per Request (CPR):
bash
# Calculate via AWS CLI
aws cloudwatch get-metric-data \ –metric-data-queries ‘{“Id”:”m1″,”MetricStat”:{“Metric”:{“Namespace”:”AWS/Lambda”,”MetricName”:”Invocations”}…}’ - Memory Utilization:90% → Increase memory
< 50% → Decrease memory - Error Burst Index:
Sudden error spikes indicate misconfigurations costing you retry fees. - Cold Start Rate:5% → Needs provisioned concurrency
Automation Tools:
- AWS Cost Anomaly Detection (Free tier)
- Datadog Serverless View ($0.10/function/month)
- Custom CloudWatch Alarms
CONCLUSION
Ultimately, embracing the principles of AWS Lambda cost optimization delivers tangible benefits, from reduced cloud bills to improved architectural design and operational efficiency. These efforts are not just about saving money; they are a vital part of building a more resilient and sustainable cloud presence. To truly understand how these specialized optimizations contribute to your organization’s overarching operational excellence and continuous improvement, consider reviewing our comprehensive guide on the DevOps Maturity Model.